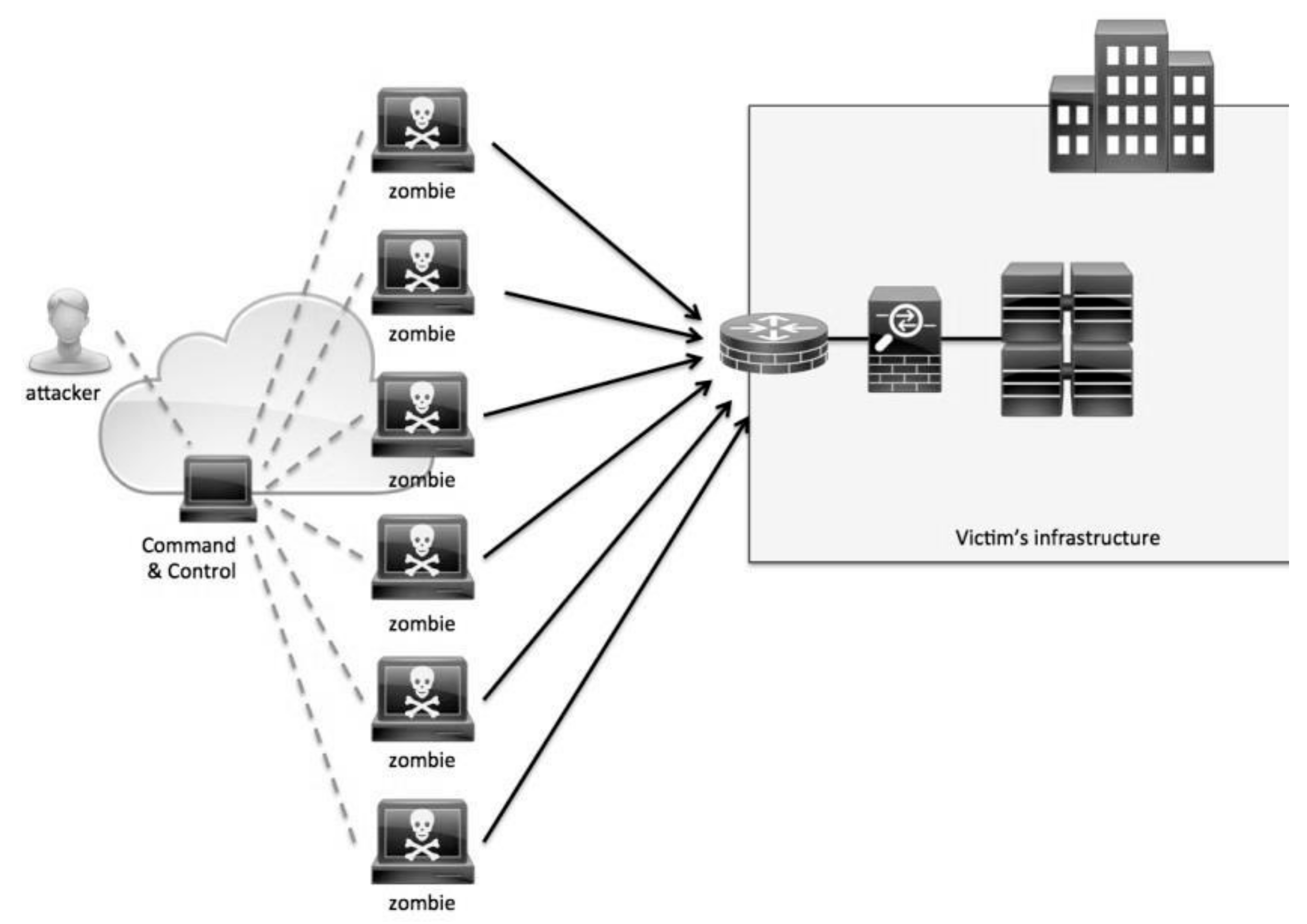
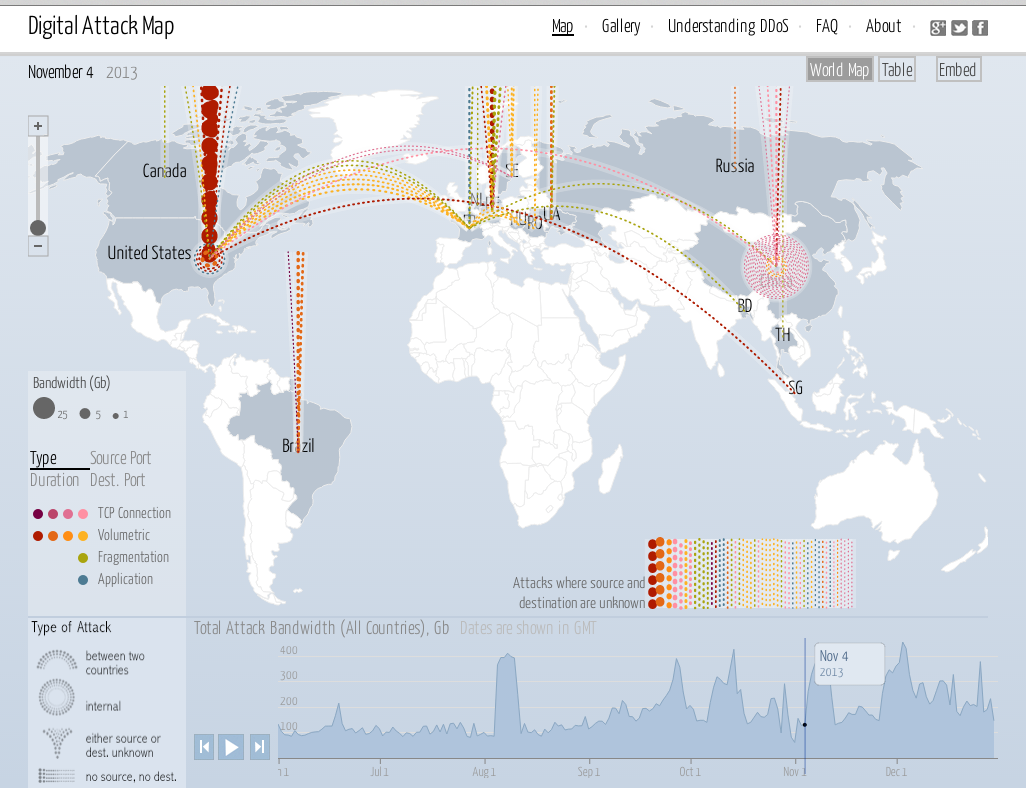
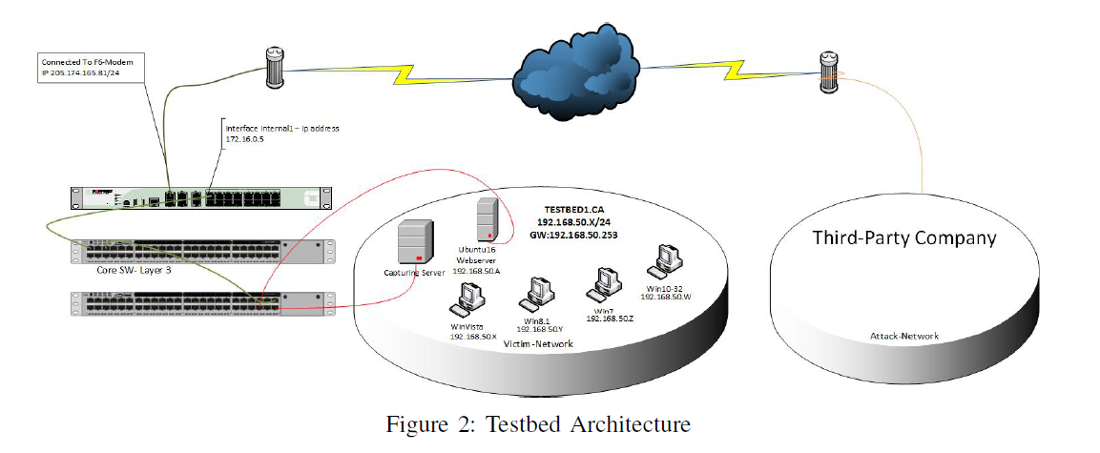
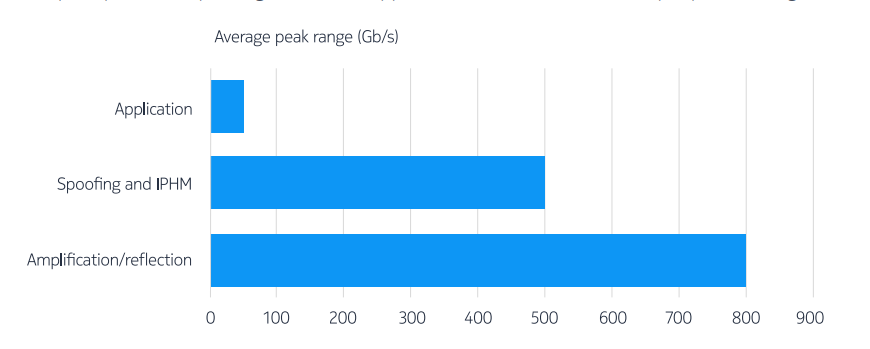
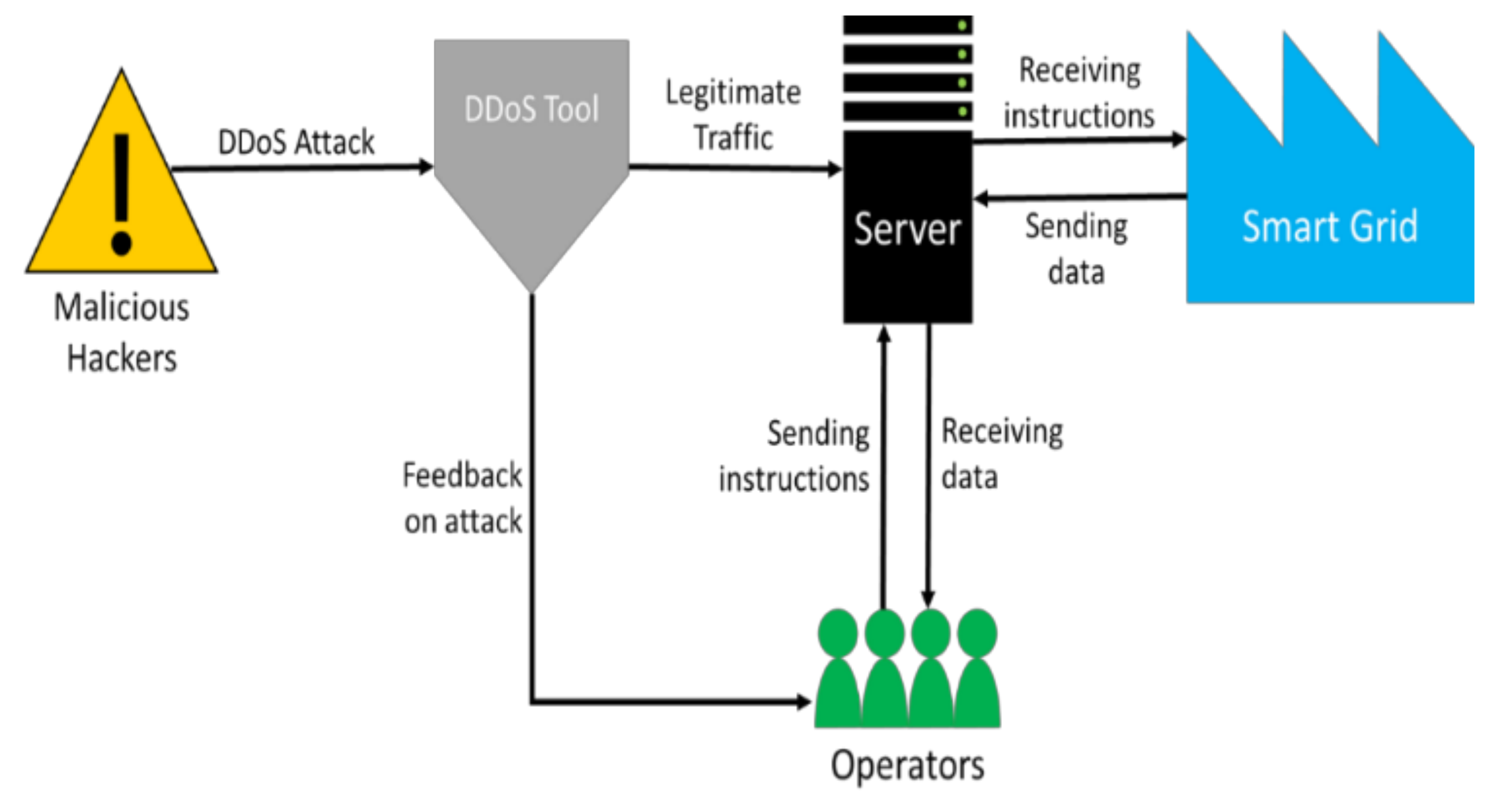
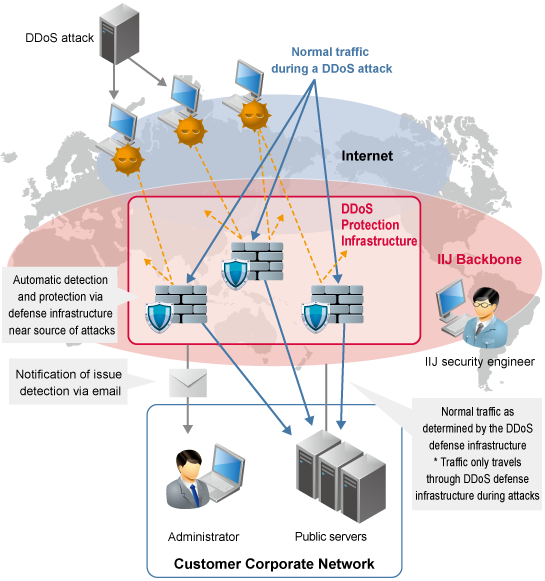
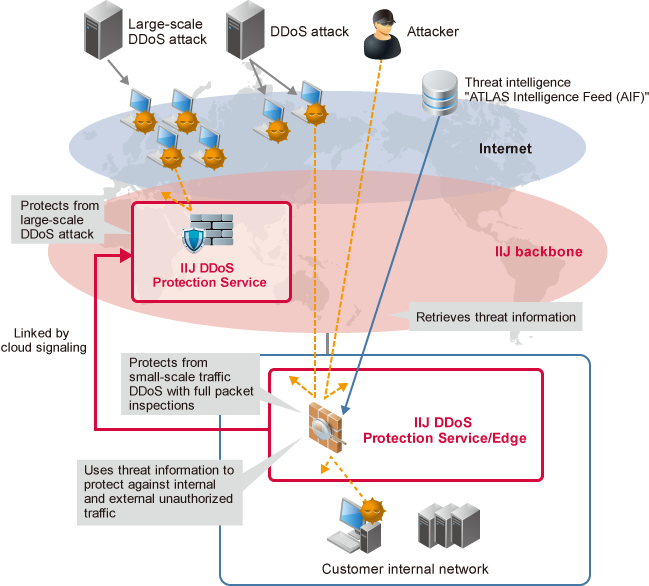
A DDoS attack scenario in IoT networks as a Botnet to target legitimate... | Download Scientific Diagram
18 Hours of Disruption: How DDoS Attacks Plagued PokerStars' High Profile WCOOP Series | Poker Industry PRO
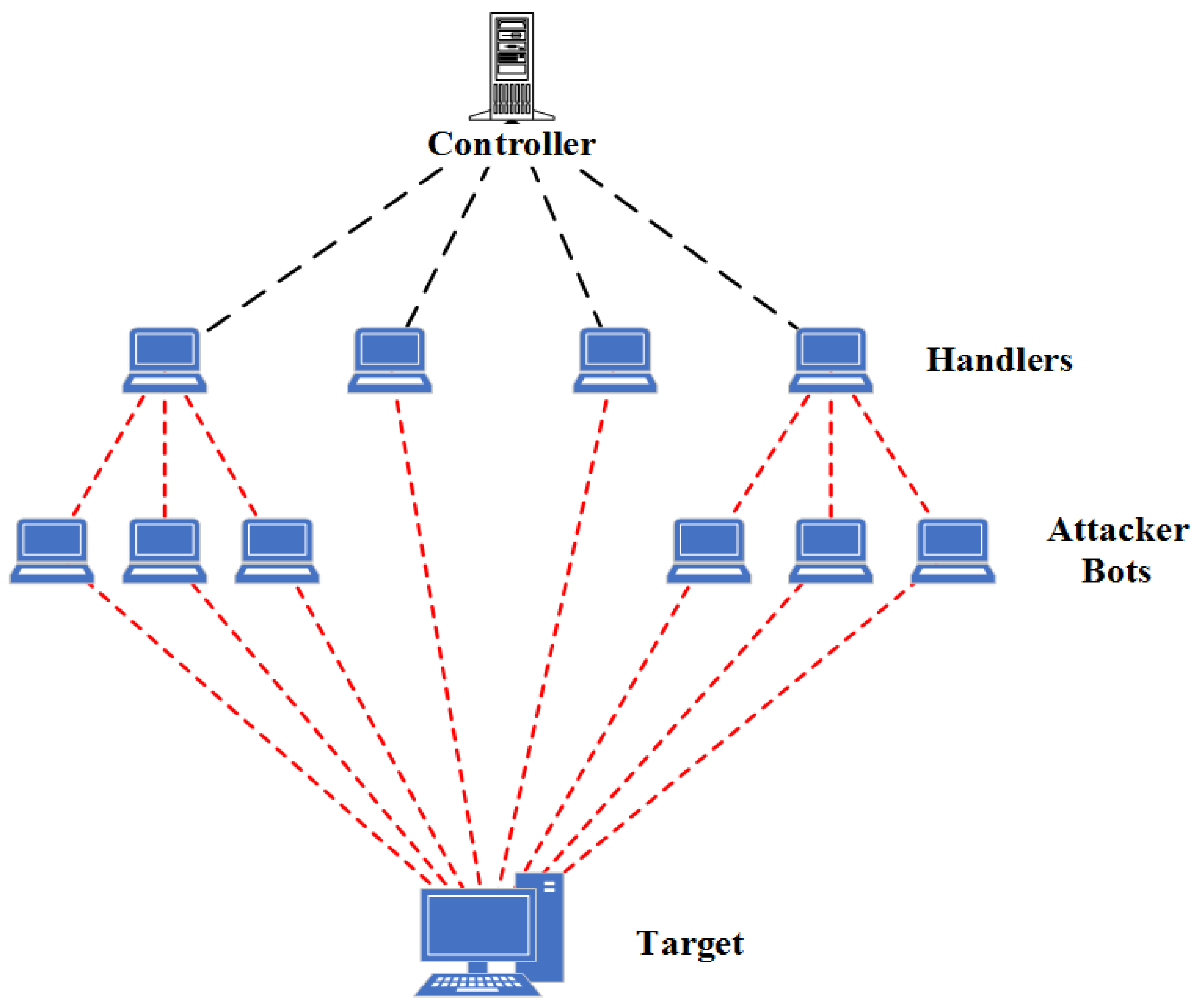
Future Internet | Free Full-Text | Effective and Efficient DDoS Attack Detection Using Deep Learning Algorithm, Multi-Layer Perceptron
Ddos Attack Color Icon Vector Illustration Stock Illustration - Illustration of bomb, virus: 206757301